Our Services
Tailored networking solutions to keep your enterprise connected and secure.




Meraki Firewall & Wireless Expertise
We provide complete deployment, tuning, and maintenance of Cisco Meraki MX firewalls and MR wireless solutions. From security policies and content filtering to RF optimization and AutoRF fine-tuning, we ensure secure, predictable, and high-quality connectivity. We also manage firmware updates, VPN configurations, site-to-site architecture, and multi-site wireless design.
Enterprise-Grade Network Design & Troubleshooting
We design, optimize, and troubleshoot enterprise networks to ensure high performance, resilience, and scalability. Our approach starts by understanding your business needs, application flows, and critical dependencies. We diagnose issues at all layers—routing, switching, wireless, security, and WAN—to restore stability and improve long-term efficiency.
Secure VPN Deployment for Remote & Multi-Site Teams
We design and implement secure VPN solutions, including site-to-site tunnels, remote access VPNs, SD-WAN configurations, and high-availability architectures. Our solutions protect traffic between branches, cloud environments, and mobile users while ensuring strong encryption, consistent performance, and centralized management.
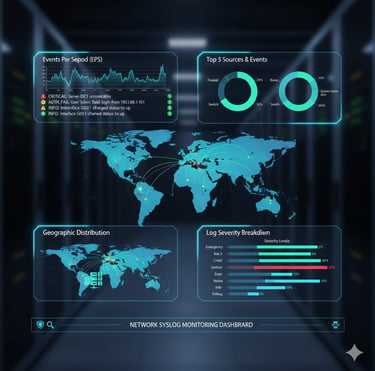
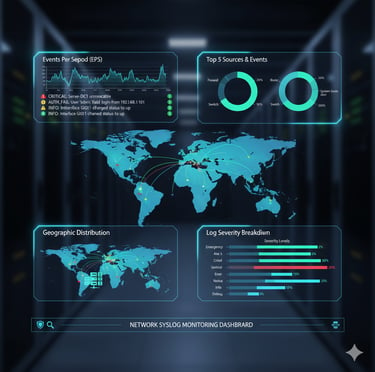
Real-Time Syslog Monitoring & Insights
We implement centralized syslog monitoring with actionable dashboards and alerts. Our service includes log correlation, trend analysis, anomaly detection, and proactive incident handling. This visibility helps detect issues before they impact business operations and supports compliance, audits, and security investigations.
Python Automation for Faster, Error-Free Operations
We automate repetitive network tasks using Python and APIs, reducing human errors and operational overhead. Automations include configuration deployments, backup routines, bulk updates, auditing scripts, and validation tools. This leads to faster execution, consistency across devices, and improved change reliability.
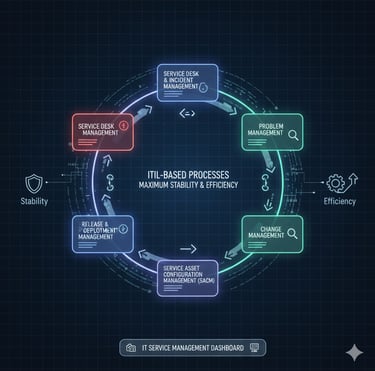
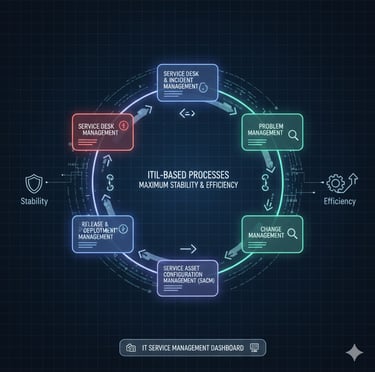
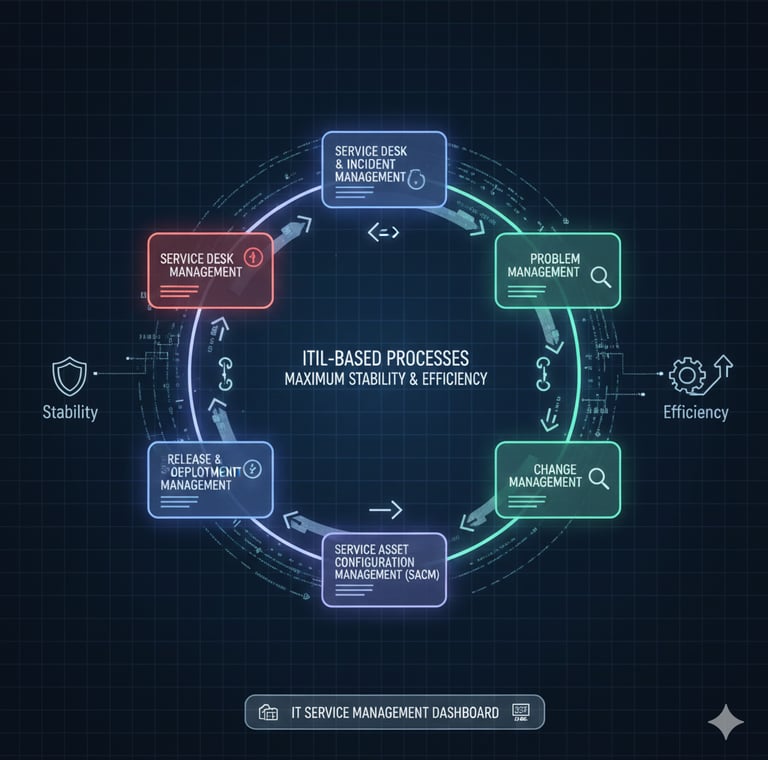
ITIL-Based Processes for Maximum Stability & Efficiency
We follow ITIL best practices across all operations, including Incident Management (P1–P4), Problem Management, Change Management, Demand & Capacity Planning, Maintenance Windows, and BAU workflows. This ensures predictable operations, controlled changes, minimized downtime, and continuous improvement—all aligned with your business priorities.


Success Cases
Real projects shaping enterprise networks.
1. BGP Multi–Data Center Redundancy
Before: Routing between primary and secondary DCs was inconsistent, causing failover issues.
Action: Optimized BGP prefix propagation with proper attribute tuning (LP, MED, AS-Path).
Result: Seamless failover, stable redundancy, and predictable routing behavior.
9. Python Automation for Troubleshooting & Compliance
Before: Manual checks were slow, error-prone, and inconsistent.
Action: Developed Python scripts for switch validation, health checks, and pattern detection.
Result: Faster troubleshooting, fewer errors, and automated compliance.
2. Pseudowires Over MPLS / Carrier Ethernet
Before: Legacy systems needed transparent L2 connectivity across carriers.
Action: Deployed pseudowires over MPLS on carrier Ethernet infrastructure.
Result: Stable, low-latency transport with full interoperability.
3. L2 and L3 Loop Detection & Prevention
Before: Intermittent outages due to undetected L2/L3 loops.
Action: Identified root causes using packet captures, spanning-tree analysis, and routing logs.
Result: Loops eliminated; network stabilized with preventive mechanisms.
4. Firewall Load Balancing for TURN/RTC Traffic
Before: Video and voice apps suffered due to poor TURN traffic handling over WAN.
Action: Tuned firewall load-balancing and NAT behaviors for real-time traffic.
Result: Improved video/voice quality, fewer timeouts, and smoother RTC performance.
5. QoS Optimization for WebRTC Voice
Before: Jitter and packet loss were degrading WebRTC calls.
Action: Applied targeted QoS policies and WAN prioritization.
Result: Consistent voice quality and reduced media degradation.
6. Enterprise-Scale Syslog + Elasticsearch
Before: No visibility into device logs; troubleshooting was reactive and slow.
Action: Deployed Elasticsearch-based monitoring processing thousands of events/sec.
Result: Real-time insights, faster root-cause analysis, and proactive alerting.
7. OSPF Area Tuning for Branch MPLS Networks
Before: Branch offices experienced routing instability and inefficient failovers.
Action: Redesigned OSPF areas and optimized default route propagation.
Result: Highly stable branch routing and predictable behavior over MPLS.
8. Carrier IPsec for Enterprise + Private Cellular SIM Networks
Before: SIM-based IoT and remote sites couldn’t reach enterprise resources securely.
Action: Built IPsec tunnels between enterprise firewalls and carrier gateways.
Result: Full secure reachability and reliable multi-network integration.
13. NOC Consulting & ITIL Process Correction
Before: Company had poor ticket handling, incorrect impact definitions, and SLA breaches.
Action: Reworked Incident, Problem, and Impact definitions aligned with business and ITIL.
Result: Better prioritization, improved SLA compliance, and more efficient operations.
And many other tailored solutions.
We are here to listen, assess, and resolve your networking challenges with precision and professionalism.
10. Enterprise Code Upgrades
Before: Devices ran outdated firmware with stability and security risks.
Action: Planned and executed code upgrades following best practices and rollback plans.
Result: Increased stability, reduced vulnerabilities, and improved performance.
11. Big-Data Edge Port Behavior Analysis
Before: Random port flapping and endpoint issues with no clear cause.
Action: Analyzed syslog patterns at scale using big-data tools.
Result: Identified misbehaving endpoints and reduced recurring incidents.
12. Packet Capture & Forensics (Elastic Search Integration)
Before: Hard-to-reproduce intermittent network issues.
Action: Performed packet captures, indexed them in Elastic, and correlated with logs.
Result: Faster RCA and improved incident resolution accuracy.





Frequently Asked
What is ITIL?
ITIL is a set of best practices for IT service management.
Do you support Meraki?
Yes, we deploy and manage Meraki firewalls and wireless solutions.
Can you automate network tasks?
Absolutely, we use Python automation to streamline network operations and reduce manual work.
What VPN types do you offer?
We provide site-to-site and remote access VPN solutions.
Do you monitor syslog?
Yes, we analyze syslog data to detect and resolve network issues.
How do you optimize network performance?
We troubleshoot and fine-tune network components to ensure smooth and reliable connectivity.
Contact
Reach out for tailored network solutions.
Phone
support@granddata.com
+52 8116406297
© 2025. All rights reserved.
